
RSA. Système de chiffrement Rivest Shamir Adleman. La cryptographie et
🔥Become A Full Stack Developer Today: https://taplink.cc/simplilearn_c_softwaredevIn this video on the RSA Encryption Algorithm, we learn about the global s.

RSA. Cryptography and Network Security. Rivest Shamir Adleman
RSA algorithm is an asymmetric cryptography algorithm. Asymmetric actually means that it works on two different keys i.e. Public Key and Private Key. As the name describes that the Public Key is given to everyone and the Private key is kept private. An example of asymmetric cryptography:
RSA. Rivest Shamir Adleman cryptosystem. Cryptography and Network
The RSA algorithm (Rivest-Shamir-Adleman) is the basis of a cryptosystem -- a suite of cryptographic algorithms that are used for specific security services or purposes -- which enables public key encryption and is widely used to secure sensitive data, particularly when it is being sent over an insecure network such as the internet.

GitHub AbdullahAlhussein/RSAAlgorithm RSA (RivestShamirAdleman
Cryptography algorithm RSA — Rivest-Shamir-Adleman. The RSA algorithm uses a pair of keys to encode and decode messages, this keys are the public and the private keys, respectively. The effectivity of this method is due to the relative facility to check that a given number is prime and to the difficulty to execute the number factoring.
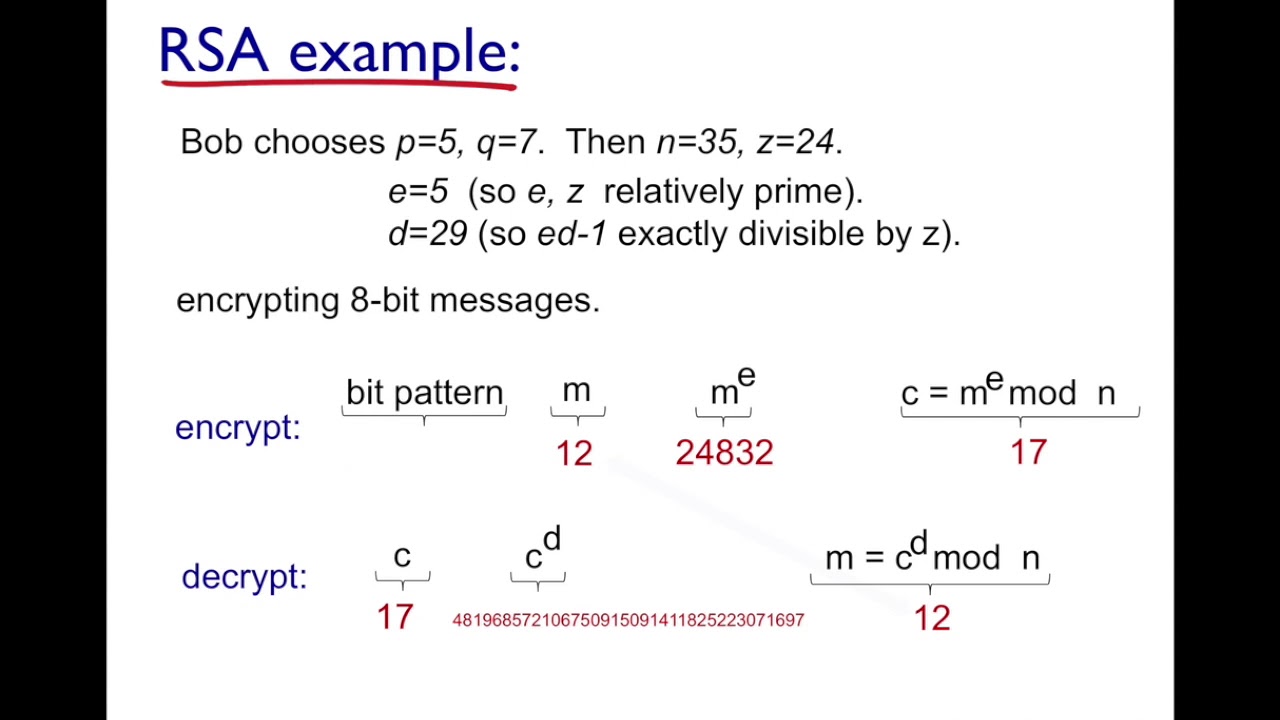
RSA (Rivest, Shamir, Adleman) Algorithm explained with example YouTube
Rivest-Shamir-Adleman public-key cryptosystem, one of the oldest widely used for secure data transmission. The "RSA" comes from the surnames of Ron Rivest Adi Shamir Leonard Adleman, who publicly described the algorithm in 1977.

Rsa rivest shamir adleman [PPT Powerpoint]
RSA (Rivest-Shamir-Adleman) is an algorithm used by modern computers to encrypt and decrypt messages. It is an asymmetric cryptographic algorithm. Asymmetric means that there are two different keys. This is also called public key cryptography, because one of the keys can be given to anyone. RSA uses a public key and private key.
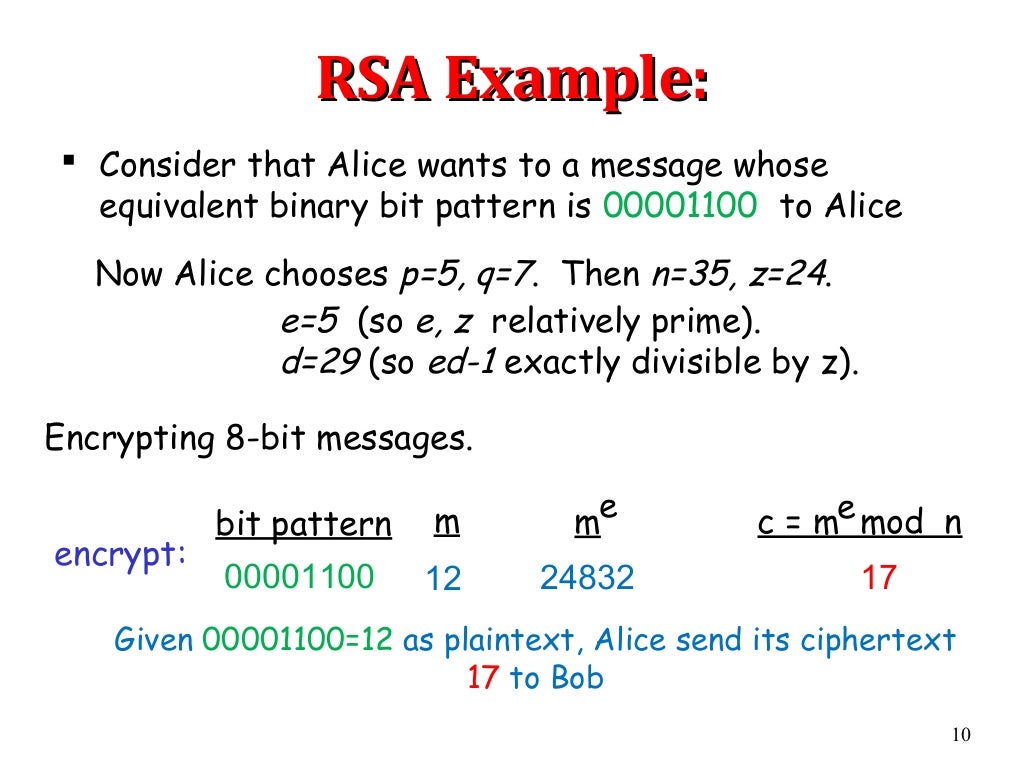
Rsa rivest shamir adleman
"It is perfectly sound and usable into the future."Part of the Giants Among Us series in celebration of RSA Conference's 20th anniversary

RSA. Rivest Shamir Adleman Cryptosystem. Cryptography and Network
Rivest Shamir Adleman (RSA) is a well-known public-key or asymmetric cryptographic algorithm. It protects sensitive data through encryption and decryption using a private and public key pair. First introduced in 1977 by Ron Rivest, Adi Shamir and Leonard Adleman of the Massachusetts Institute of Technology, RSA is named after their last initials.

RSA. Cryptography and Network Security. Rivest Shamir Adleman
RSA is an acronym for the inventors' names Rivest, Shamir, and Adleman. It is a public-key cryptographic algorithm based on the computational complexity of the large prime factorization problem. The idea of an asymmetric public/private key cryptosystem is attributed to Whitfield Diffie and Martin Hellman who published the concept in 1976.

RSA Sistema Criptogr?fico De Rivest Shamir Adleman Seguridad De La
The RSA algorithm was invented by three MIT professors, Ronald Rivest, Adi Shamir and Leonard Adleman in the summer of 1977 [21], meeting the challenge put forward by the Stanford team Whitfield Diffie, Martin Hellman and Ralph Merkle in 1976.

Nombres premiers et cryptologie l'algorithme RSA Interstices
The Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. Asymmetric encryption uses a key pair that is mathematically linked to enc r ypt and decrypt data.

The hybrid cryptosystem based on zigzag and rivest Shamir Adleman
RSA is a public key cryptosystem by Ron Rivest, Adi Shamir, and Leonard Adleman. This article is an introduction to using RSA in Crypto++. For more information on encryption schemes, visit RSA Encryption Schemes. For more information on signature schemes, visit RSA Signature Schemes. Raw RSA provides information about low level RSA operations.

RivestShamirAdleman (RSA) Cybersecurity Glossary
Rivest-Shamir-Adleman Rivest-Shamir-Adleman short form as RSA falls under the Asymmetric Encryption category. Thus, in RSA the sender and the recipient of the data use a different key for encryption and decryption. RSA was invented in 1978 and is considered the most secure way of encrypting data.

RSA (Rivest, Shamir, Adleman) YouTube
The Rivest-Shamir-Adleman (RSA) algorithm is the most widely accepted approach in asymmetric cryptography. Asymmetric cryptography means that one key is used to encrypt and a different, but related one is used to decrypting the message. The RSA algorithm is as follows: Choose p, q, two prime numbers Calculate n = pq Calculate f (n) = (p-1) (q-1)

RSA. Rivest Shamir Adleman cryptosystem. Cryptography and Network
To review the RSA algorithm for public-key cryptography To present the proof of the RSA algorithm To go over the computational issues related to RSA To discuss the vulnerabilities of RSA Perl and Python implementations for generating primes and for factorizing medium to large sized numbers CONTENTS Section Title Page

Gallery Laboratory for Molecular Science
RSA (Rivest-Shamir-Adleman) is a public-key encryption algorithm that was developed in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman. RSA is widely used for secure communication, digital signatures, and encryption of sensitive data RSA encryption is based on the difficulty of factoring large integers, which makes it very difficult to.